Note: if the AD Recycle Bin isn’t already enabled in your forest then you need to dig out your last system state backup and go through the restore process – enabling the ADRB does not help with recovering any objects deleted prior to it being enabled. See this article for enabling it.
A VM snapshot can potentially be used to restore from for DR purposes but only if *both* the virtualization host platform and the underlying guest OS supports it (W2k12 or later for the guest OS and Hyper-V W2k12 or vSphere/ESXi 5.0 Update 2 for the virtualization hosts).
If your VM snapshot doesn’t fulfil the minimum OS and virtualization requirements then you may still be able to use it as a last resort but the operation will be a lengthy process if the snapshot DC was brought online before manually setting the “Database Restored from Backup” registry key on it to force it to generate a new invocation ID.
From the VMware article on VM-GenerationID support:
VM-Generation ID functionality requires the hypervisor vendor to create the virtual machine identifier and expose it to the guest. VMware has provided this functionality in the following releases of vSphere:
- VMware vSphere 5.0 Update 2 (vCenter Server and ESXi must both be at 5.0 Update 2)
- VMware vSphere 5.1 (ESXi must be at least 5.0 Update 2)
From the Technet article on Safe Domain Controller Virtualization:
Beginning with Windows Server 2012, AD DS virtual domain controllers hosted on hypervisor platforms that expose an identifier called VM-Generation ID can detect and employ necessary safety measures to protect the AD DS environment if the virtual machine is rolled back in time by the application of a VM snapshot. The VM-GenerationID design uses a hypervisor-vendor independent mechanism to expose this identifier in the address space of the guest virtual machine, so the safe virtualization experience is consistently available of any hypervisor that supports VM-GenerationID. This identifier can be sampled by services and applications running inside the virtual machine to detect if a virtual machine has been rolled back in time.…………….Virtualized domain controller cloning relies on the hypervisor platform to expose an identifier called VM-Generation ID to detect creation of a virtual machine. AD DS initially stores the value of this identifier in its database (NTDS.DIT) during domain controller promotion. When the virtual machine boots up, the current value of the VM-Generation ID from the virtual machine is compared against the value in the database. If the two values are different, the domain controller resets the Invocation ID and discards the RID pool, thereby preventing USN re-use or the potential creation of duplicate security-principals.
Let´s look at the AD Recycle Bin in action in a lab:
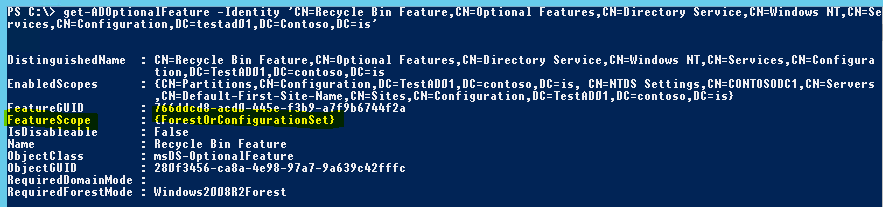
First, we check whether the AD Recycle Bin feature is enabled in my lab forest using the following Powershell command:
get-ADOptionalFeature “Recycle Bin Feature”
If the EnabledScopes part is empty it means the AD Recycle Bin still hasn’t been enabled in your AD forest, luckily I already have it enabled in my lab.
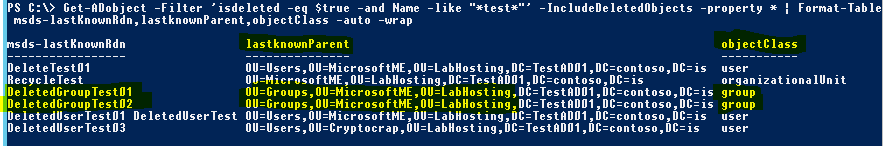
Now, I just deleted a few items from my AD lab, some of which shouldn’t have been deleted and now need to be restored quickly. I know all the deleted objects had ‘Test’ in the name so let’s see what shows up in the AD Recycle Bin when searching for objects with the isDeleted AD attribute set to ‘true’ and that include Test somewhere in the name and then sorting the list by the AD attributes msds-lastKnownRdn and lastknownParent to see where they were originally deleted from:
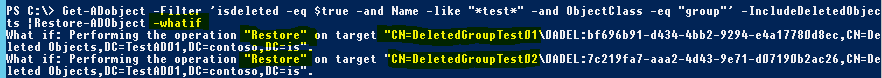
Of these 6 items, I’m only interested in restoring the group objects (the other ones were intentionally deleted). I’ll add a filter to only target groups and then pipe it to the Restore-ADObject Powershell command with the -WhatIf switch appended to determine what action would be performed on which objects without actually performing the restore:
Great, the -WhatIf option shows me the command would restore only the two groups that I want to restore and leave everything else we don’t want to restore still in a deleted state in the AD Recycle Bin. We can now confidently run the same command again without the -WhatIf switch (Adding the -Verbose option instead to report the status for each restore):
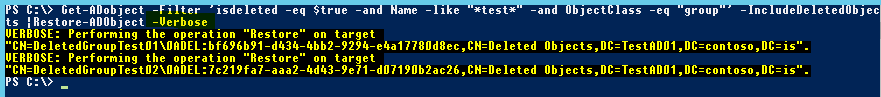
Excellent! The two groups and their pre-deletion membership state are now back in business without having to bother with a lengthy restore process! Let’s confirm the groups are really back in the correct OU in AD by running Get-ADObject again without the ‘isDeleted’ filter option:
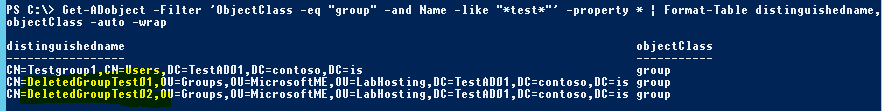
The undeleted groups are back where they belong in AD with the correct membership in the minimum amount of time required to recover from the original error.
This will of course *not* replace your regular backup procedures but it should really be considered a mandatory precaution to enable it in any AD environment running Windows 2008 R2 DC’s as it really cuts down the time required to recover from accidental deletion of objects in AD.
In W2k12 R2 there is now also the option of using the Active Directory Administrative Center to undelete objects if you want a more graphical way of doing things:
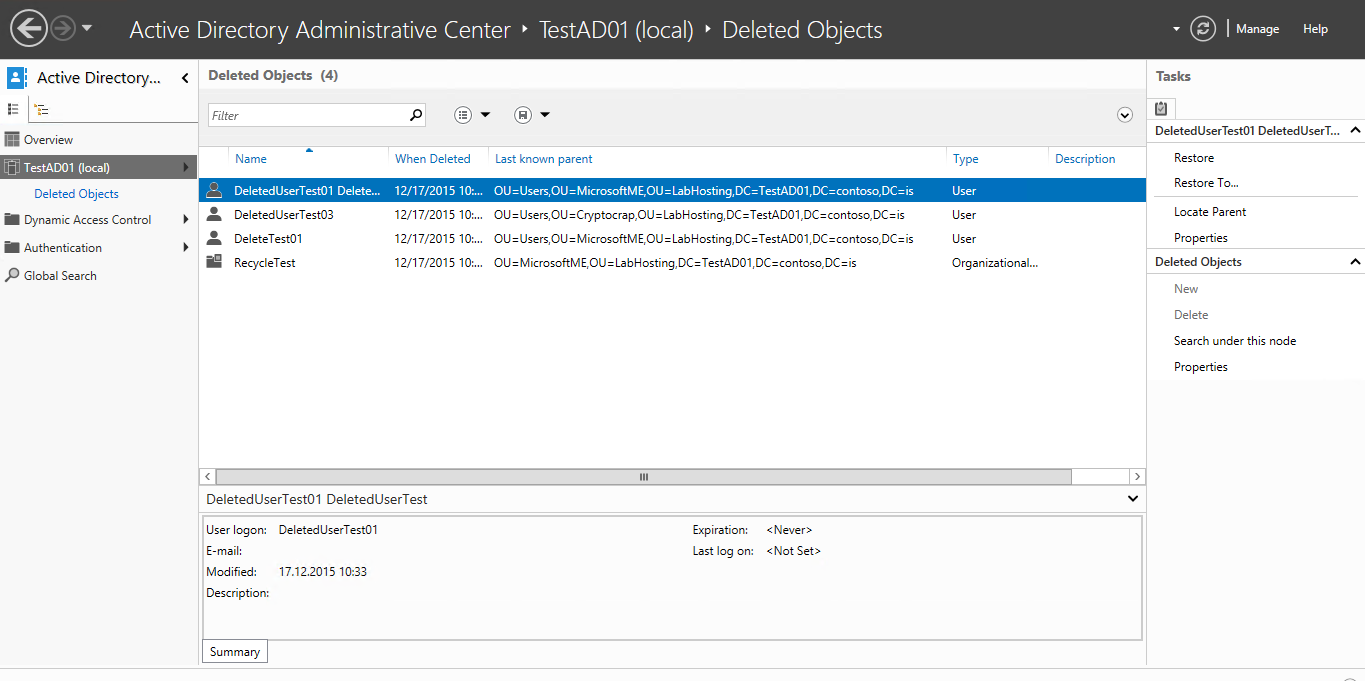
Additional links:
AD Recycle Bin Best Practices
http://blogs.technet.com/b/askds/archive/2009/08/27/the-ad-recycle-bin-understanding-implementing-best-practices-and-troubleshooting.aspx
AD Recycle Bin behaviour
http://blogs.technet.com/b/instan/archive/2010/05/10/ad-recycle-bin-and-the-conspicuously-cloned-user-accounts-conundrum.aspx
Safe virtualization of Domain Controllers
https://technet.microsoft.com/en-us/library/hh831734.aspx#safe_virt_dc
vSphere versions required for VM-Generation ID support
https://blogs.vmware.com/apps/2013/01/windows-server-2012-vm-generation-id-support-in-vsphere.html
Fixing When Your Domain Traveled Back In Time, the Great System Time Rollback to the Year 2000
http://blogs.technet.com/b/askpfeplat/archive/2012/11/23/fixing-when-your-domain-traveled-back-in-time-the-great-system-time-rollback-to-the-year-2000.aspx
Virtualized Domain Controller Architecture
https://technet.microsoft.com/en-us/library/jj574118.aspx