A quick PowerShell script to check your server environments for EternalBlue/WannaCry/Petya patching status:
A quick PowerShell script to check your server environments for EternalBlue/WannaCry/Petya patching status:
Make sure you are reading a raw string: i.e. (Get-Content JsonFile.JSON -raw) | ConvertFrom-Json
PowerShell seems to use an outdated Newtonsoft.Json.DLL file which doesn’t fully support comments
Make sure there are no comments in the .JSON file – if there are any you may need to manually edit them out to get ConvertFrom-Json to behave
The two versions being used on Azure VM’s seem to be 5.0.8.16617 (October/2013) and 6.0.3.17227 (February/2014).
Support for comments in JSON files in Newtonsoft.Json.DLL was first added in version 5.03 from 2014/11 (support for single line comments) and expanded on in later versions (6.07+)
The latest version of Newtonsoft.Json.DLL is 10.0.2 (as of April/2017)
If you put a comment into a Json file and try to run ConvertFrom-JSON in PowerShell on it you will get the following error message:
ConvertFrom-Json : Invalid object passed in, ‘:’ or ‘}’ expected. (1): {
At line:1 char:28
+ Get-Content .\config.JSON |ConvertFrom-Json -Verbose
+ ~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [ConvertFrom-Json], ArgumentException
+ FullyQualifiedErrorId : System.ArgumentException,Microsoft.PowerShell.Commands.ConvertFromJsonCommand
An Introduction to JavaScript Object Notation (JSON) in JavaScript and .NET (February 2007)
http://www.newtonsoft.com/json
https://github.com/JamesNK/Newtonsoft.Json
 Previously, support for MFA in O365/AzureAD/Skype/Sharepoint was limited to Office applications that supported it and browser-based administration of O365/Azure.
Previously, support for MFA in O365/AzureAD/Skype/Sharepoint was limited to Office applications that supported it and browser-based administration of O365/Azure.
This changes with version 1.1 of the Azure AD PowerShell module released earlier this month which provides support for MFA.
The steps to enable it are as follows:
Note: There are still some aspects in the Windows OS that are still not really aware of MFA, particulartly the Domain Join functionality. If have enabled MFA on the account you’re using for the domain join operation and you receive an erroneous “Incorrect Password” error (i.e. code 0x52e in the NetSetup.log debug log) during a domain join (and assuming you are actually typing in the correct password) then you may need to revert back to using a separate non-MFA account – at least for the domain join operation.
The Office 365 tenant/resource host (Exchange Online, SharePoint Online and Skype for Business Online) will need to be configured to accept a modern authentication connection.
Here is the per service state of modern authentication by default :
Once you have MFA enabled and the new version of the AAD PS module installed you should be able to go through the additional MFA verification steps after logon: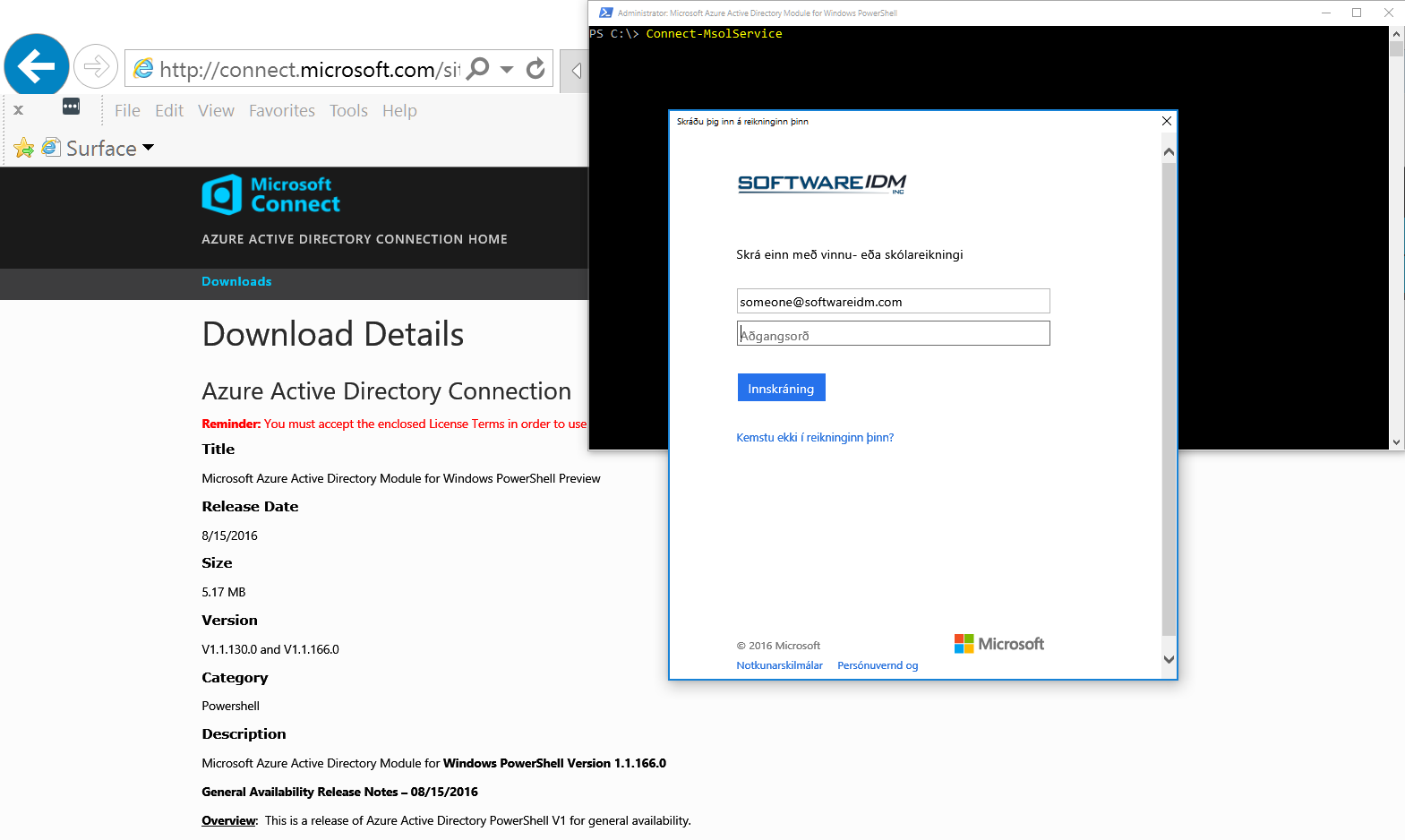
Details:
Azure Active Directory PowerShell with Modern Authentication
http://connect.microsoft.com/site1164/content/content.aspx?ContentID=32016
Download Details: Azure Active Directory Connection
http://connect.microsoft.com/site1164/Downloads/DownloadDetails.aspx?DownloadID=59185
Azure AD PowerShell: Public Preview of support for Azure MFA + new Device Management Commands
Azure AD PowerShell: Public Preview of support for Azure MFA + new Device Management Commands
How to install and configure Azure PowerShell
https://azure.microsoft.com/en-us/documentation/articles/powershell-install-configure/
Skype for Business Online: Enable your tenant for modern authentication
http://social.technet.microsoft.com/wiki/contents/articles/34339.skype-for-business-online-enable-your-tenant-for-modern-authentication.aspx
Exchange Online: How to enable your tenant for modern authentication
http://social.technet.microsoft.com/wiki/contents/articles/32711.exchange-online-how-to-enable-your-tenant-for-modern-authentication.aspx
The sign in experience with Azure Multi-Factor Authentication
https://azure.microsoft.com/en-us/documentation/articles/multi-factor-authentication-end-user-signin/
Remote Desktop Gateway and Azure Multi-Factor Authentication Server using RADIUS
https://azure.microsoft.com/en-us/documentation/articles/multi-factor-authentication-get-started-server-rdg/
What are App Passwords in Azure Multi-Factor Authentication?
https://azure.microsoft.com/en-us/documentation/articles/multi-factor-authentication-end-user-app-passwords/
Have you ever had the pleasure of being awoken in the middle of the night by a low disk space alert on one of your business-critical LOB systems?
Did you ever wish for a more proactive method for catching this than waiting for the yellow/red alerts to go “ping!”?
I know I did, so I sat down and played math for a couple of hours and then applied the result using Powershell and a scheduled task. The result is a configurable script that sends you an email alert when the sustained disk consumption on the system is estimated to consume all freespace on one of the disks within the set amount of time you specify (by default 30 Days).
Download ChkBurn 0.8 – modify all references to Contoso to fit your domain.
Sample output:
You want to find specific events from multiple archived event logs.
EventScrape.ps1 – uses Powershell Get-WinEvent to parse offline event logs and sort them into chronological order.
[array]$TotalSearch=””
# *App* is targeting archived Application logs – change to suit your needs
Get-ChildItem -include *App*.evt,*App*.evtx -Path E:\EventLogs\Winevt\logs\ -recurse |
ForEach-Object {“Parsing $($_.fullname)`r`n”
Try {
$TotalSearch+=Get-WinEvent -FilterHashtable @{
Path=$_.fullname
Id=15004;
#StartTime=”1/14/2011″ ; #in case you want to limit the search to a certain time range
#EndTime=”1/15/2016″
} -EA Stop
$TotalSearch+=Get-WinEvent -FilterHashtable @{
Path=$_.fullname
Id=15005;
#StartTime=”1/14/2011″ ; #in case you want to limit the search to a certain time range
#EndTime=”1/15/2016″
} -EA Stop
} Catch [System.Exception] {“Done”}}
$TotalSearch| sort-object TimeCreated|fl|out-file “BackPressure.txt”
$searchCSV=$TotalSearch| sort-object TimeCreated|convertto-csv -useculture
$searchCSV|out-file “SearchCSV.csv”
gc .\BackPressure.txt |select-string “resource pressure” -context 5,7 |out-file Presures.txt
invoke-item .\Presures.txt
Details:
Use PowerShell to Parse Saved Event Logs for Errors
http://blogs.technet.com/b/heyscriptingguy/archive/2011/01/25/use-powershell-to-parse-saved-event-logs-for-errors.aspx